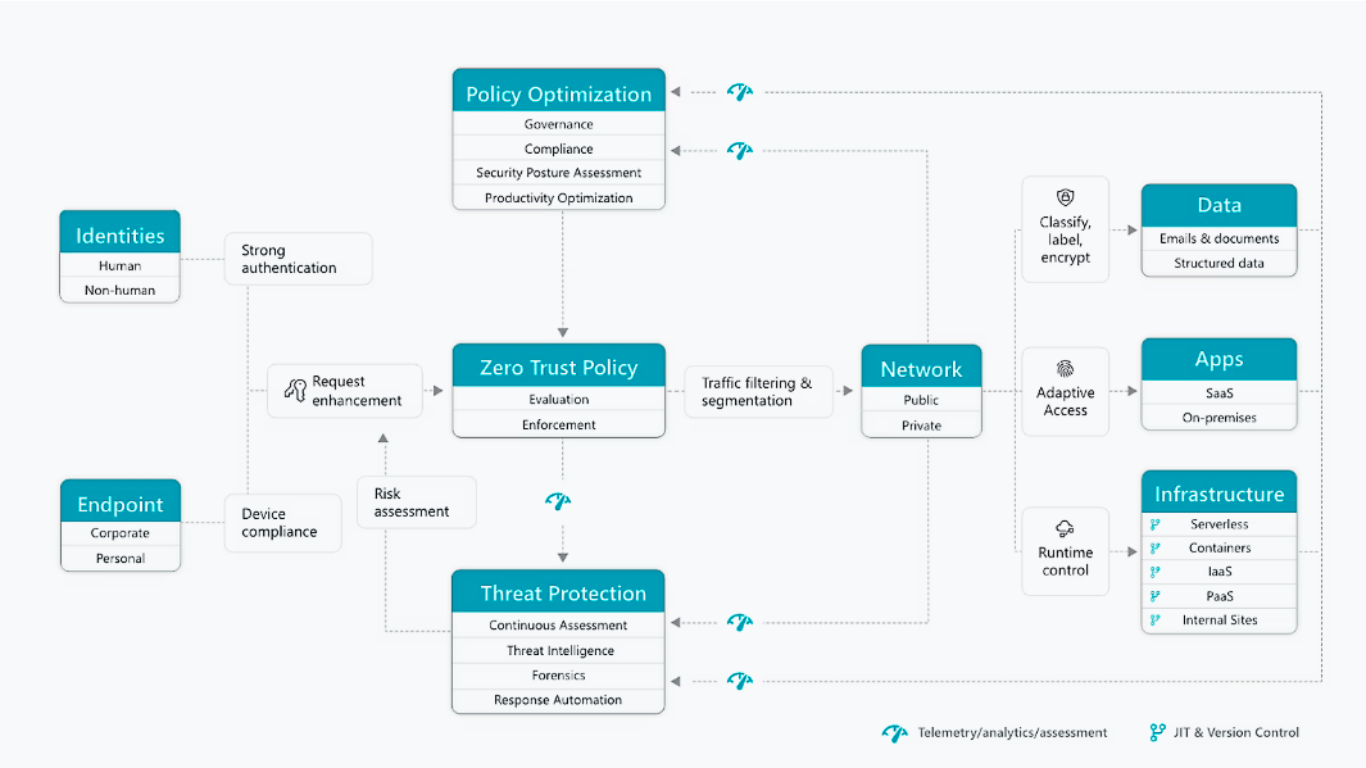
Zero Trust is a security model that assumes no implicit trust within a network. It requires a security framework with advanced technologies such as risk-based multifactor authentication, next-generation endpoint and cloud workload protection, and robust real-time monitoring and response capabilities to catch malicious activity.
A zero-trust strategy minimizes your attack surface, reducing the likelihood of a breach. It also requires continuous verification and a hardened estate that can withstand violations when they occur.
Authentication
With remote work trends increasing, multiple layers of security are needed to protect sensitive applications, data, and infrastructure. A zero-trust approach allows organizations to implement a more resilient cybersecurity model that mitigates risk across the entire network.
The first pillar of zero Trust is authentication. This includes multifactor authentication (MFA), digital certificates, and other methods to verify identities and secure connections. Digital certificates provide a way to validate identity and prove the authenticity of a resource or entity, similar to how a driver’s license, passport, or piece of paper currency can be verified as genuine.
Next, a Zero Trust environment uses a combination of identity access management, network security, and device and endpoint security controls to eliminate the trust boundary within the enterprise network. This approach minimizes the attack surface by reducing the “blast radius” in case of an external or insider breach using micro-segmentation and granular perimeter enforcement based on data, user, and location.
Least-privilege access is also a key component of Zero Trust as it helps reduce the number of ways an attacker can enter sensitive information like proprietary data, customer records, or financial transaction details. An organization must utilize authentication and encryption technologies like PKI to enable least-privilege access.
Microsegmentation
A Zero Trust architecture uses micro-segmentation to create granular perimeter enforcement and secure connections for devices, users, applications, and data. It minimizes lateral movement of threats and lowers the chance that an attack will spread across your network.
Today’s complex networks consist of multiple environments, including remote workers using VPNs, employees connecting to cloud apps, developers producing code in DevOps, all departments automating processes with RPA, and countless IoT and OT devices connecting to systems. Managing the security of all these identities can be challenging for overburdened IT teams.
Zero Trust models use micro-segmentation to establish secure connections for each device, user, or application based on its unique attributes and associated risks. These include, for example, identifying the most sensitive data within your organization. This allows you to isolate and protect these assets and create access control rules based on specific types of traffic, reducing the chance that a breach will spread across the entire network.
Unlike traditional defense strategies that protect the perimeter, Zero Trust is about securing your organization’s most critical assets. This is accomplished by creating smaller segments or zones within your network and requiring that each zone be verified individually. If one zone is compromised, an attacker will find it difficult to move laterally across the network and expose additional zones or even your internal data.
Continuous Verification
As attackers become more sophisticated and the threat landscape continues to evolve, Zero Trust is a security model that focuses on minimizing the attack surface for your organization by verifying every user, device, and network connection before trusting them. This can be done through a proxy-based architecture that terminates each connection before it enters the infrastructure, allowing additional controls, such as identity verification and using the least privilege principle.
IT teams will build processes to identify new vulnerabilities and threats during this phase. They’ll also work to develop protocols that allow them to detect and stop attacks before they cause damage. This can be done by implementing advanced threat protection solutions that provide unique, unified visibility and protection across hybrid-cloud environments through an inline cloud access security broker (CASB), data loss prevention (DLP), secure web gateway (SWG), and ATP.
The hybrid work trends of today’s enterprise include remote workers connecting to the office from home or on the go, developers working in multi-cloud and DevOps environments, IoT devices connecting to networks, and many other connections that create an ever-expanding attack surface for IT teams. It is nearly impossible for overburdened IT teams to control who has access to company information and resources as these trends continue to expand, making a zero-trust approach an essential cybersecurity strategy.
Assume Breach
There’s no such thing as 100% security, so organizations should have a plan to detect, respond, and mitigate when threats do enter their ecosystem. This plan should include deploying the “assume breach” mindset, which focuses on continuously scanning the entire organization’s ecosystem to quickly identify anomalies and threat activity that suggest an internal attacker is at work. This allows an attack to be stopped more quickly and minimizes the impact of a breach.
Taking an assumed breach approach starts with tightly controlling access and permissions for every identity — including remote workers, mobile devices, IoT devices, software developers in DevOps environments, cloud service users and providers, RPA bots, and more. This requires implementing Zero Trust architecture. This approach closes vulnerabilities exploited by cyber attacks, malicious insiders, and lateral movement in the network once they have gained entry.
It also helps to implement the “least privilege principle,” which ensures that each device is given only the minimum level of Trust required to function — so that when one of these devices becomes compromised, it can’t spread malware and attack other systems in your ecosystem. Finally, it’s important to test your systems regularly so that you know they’re working properly and are protected against the latest cyberattacks. It would help if you also tried using a range of scenarios to prepare you for whatever the threat landscape brings.

The Search Engine Cage team is on a mission to educate entrepreneurs. We make things easier for the small business owner, by writing articles that help them to understand SEO and Digital Marketing.